
January 1999 - Vol 15 - Issue 1
Newsletter - Internet Edition



Dear Friends,
God calls us to witness in HIS name to our brothers and sisters in the world, to teach what it means to know Christ as their Lord and Savior. “My mouth shall speak the praises of the LORD…” Psalm 145:21
It is with regret that I inform you that I’m leaving, and will no longer be the editor of the newsletter. This issue was already done by my mother, Sherry Nisly, who will be requesting the board to approve her as the new editor, unless there is someone else who would like to request the position.
It is with great excitement that I tell where I will be going. I’ll be leaving for overseas to go do God’s work. Hopefully this will also help me grow as an individual, strengthening me in my own Christ-Like walk. I will be leaving for a Missions trip to Thailand for 15 months. It will be three months of training in Salunga, PA followed with twelve months of service and evangelism in Thailand. I will be going through EMM (Eastern Mennonite Missions) working with their YES team (Youth Evangelism Service). The group I will be working in will consist of 4-7 people, ages 18-30 years old, and will be working primarily with youth. My leave date is February 14, just over a month away.
For those who are not familiar with me on a personal basis. I’d like to tell you a bit about me. I am now 24 years old, and have an Associates Degree in Visual Communications Specializing in Photography. Currently I work full time at Gene’s Camera Store doing computer graphics. I attend Brenneman Memorial Missionary Church in Goshen, where I help our two youth pastors, Russ and Kevin. I’m a group leader for Junior High youth Wednesday nights and recently enjoyed going to 3DYC (3-District Youth Convention) with them. I have worked with youth for 4 years (the first 2 were at Liberty Community Church, also in Goshen), and I really enjoy it. This experience is going to be such a growth time for me I am really eager to go, but reluctant to leave for I enjoy working with Russ and Kevin, and of course, have enjoyed working on the newsletter. I have learned a lot while working on it, and hope you have enjoyed reading it.
As I anticipate leaving, I ask two things of my friends and family. The first being prayer as it should be the focus of all things we do. It brings God to the center of it all where He should be. By praying for me you help me do just that, bring God to the center of it all. I also need to raise $7,500. This is a lot to raise in just a short amount of time but God willing, it will happen. In whatever way you can support me would be a great help to me. I have about a month to raise the funds and you can help by making a one-time contribution or a monthly pledge amount and send the check monthly. By supporting me in this you share in the work and ministry that will be done with the people of another nation. This is really exciting to me and I hope you choose to be part of it too.
Sincerely,
Eric A Nisly
318 S. 10th Street
Goshen, IN 46528-3514
 Top
Top
If you had asked Jocelyne and me at 3:00 p.m. on December 3rd how games night was going to go, either of us would have said terrible. Russ had just called to say that my Windows NT 4.0 machine from work could not be used for the games from Microsoft. The spare Windows 95 system at work was loaned out earlier in the day. I had to go to Davenport College for class, and we were 3 computers down at that point.
Sounds bleak, doesn’t it? I am sure Russ was about ready to give up and quit being the program director. Microsoft was coming, and neither Russ, Jocelyne, or I knew how it was going to turn out. I called several people to see if they could help, and they came to the rescue.
Gloria Savill and Marty Mielke brought a computer from work to cover one of the gaps. Eric Nisly was able to bring a computer that was listed as out-of-service earlier in the week, and Bill Van Patten was able to bring some parts that we needed to get us through. With their help, we had 9 computers running games at the appointed time.
Clark Miller from Microsoft was there with a very impressive Motocross Madness game that used a new game stick. We displayed this game on the screen with the projector provided by Rent-A-Bit to give everyone the full effect. The new game stick used accelerometers that sensed if you were turning left or right, pulling back or pushing down. The buttons controlled speed. This new game controller gives a new feeling to the games. Connected only by a thin wire, you have more freedom of movement.
Watching from the back of the room as Bill (Wild Thing) Van Patten rode that cycle across the desert and off into the sunset was something to see. Bill used every bit of body English he could to stay on that horse. After some spectacular crashes, he turned the controls over to the younger kids, who crashed more often but would have walked away in real life. Bill seemed to forget he was riding a cycle, not flying an airplane. Bill needed a parachute to live through some of his crashes.
Microsoft also brought Combat Flight Simulator. They have added several new airplanes to this old standby, and now you can enter combat in fighters from World War I to the Persian Gulf. With a joystick, this was as close to flying in combat as either of us have seen on a PC.
The last game from Microsoft was Age of Empires and they had the new expansion pack. We had a young man who was an expert on the game who made it look easy. I guess Jon is not made of the stuff to take over the world, he was crushed quickly. Just not the megalomania type, I guess. Of course, if he had watched how to play the game before he tried, it would have helped.
The other games playing were:
1. Laser Chess
2. MDK (kill the bad guys)
3. Microsoft Flight Simulator 98 (1st hour)
4. Monty Python, “Quest for the Holy Grail”
5. Microsoft Golf 98
6. Diablo
7. Software by the Foot, games for children (2nd hour)
We did not have an auction this year, but we did have some very good door prizes. Microsoft supplied three new games and Xcel Computer Systems donated a 56k Zoom modem. I am sure that Jon did not have to twist Kevin McCarthy’s arm too hard.
We want to thank those people who came through at the last minute to help make this year’s game night a success. Next year, if you want a bigger and better Games Night, then we need people other than the old standbys to bring in their computers. Russ Burke brought two computers, including one that was not running at 6:00 p.m. the night before. All told, the EPCUG board brought 8 of the 10 computers that we used. If the members want more computers and more games next year, then we need people to get out of their seats, and come and show off their gaming skills.
One system brought to games night was not running and Jon did not have time to fix it during the evening. Gee, Jon should be able to set up 3 computers, load games on 4 computers, fix the system that was not working, and eat supper all in the 26 minutes from when he arrived from college until the meeting started. Oh well, guess he is only human.
 Top
Top
As tax time gets closer and closer, we all must face that awful responsibility of gathering together information that may be scattered all over the place.
WANT SOME HELP? Many of you have already used “TurboTax”, the premier tax preparation program for you and I. The February program will feature the latest version for you to see. If we are all good boys and girls, we may find a few copies to spread around also. Plan to attend!
 Top
Top
|
 Top
Top
It has been a long time since I wrote the last Y2K article for the newsletter. Because I had to go back and review where we are now, it would probably be good for us all to review.
The first article in the series in July talked about how we got into this mess in the first place. Removing the two digits from the date reduced entering errors and reduced the amount of memory required. An example is the Veterans Administration in the early 1960s had over 45 million people to track. Removing the two digits from the date saved 90 million bits of file space. This is 90,000 kilobits of information when 1KB of memory cost $1000 each. The reduction saved the American taxpayers $90,000,000 in computer expenses. Big deal, the cost to fix the problem will be into the billions!
The second article covered how Y2K can affect both you and I. This included things like credit cards, your bank, and other problems we all may have. I tried to be fair, but since then many experts have come out saying that I was optimistic about some of my projections. Just as many have come out saying that I was very pessimistic, so I figure I am about in the middle.
The third article in September covered how to get your hardware Y2K ready. We discussed the five levels of Y2K preparation. The article covered several hardware options ranging from software fixes to hardware fixes. In this article I first warned that not all the new computers in the stores are Y2K ready. Since then the state of Wisconsin has sued several of the computer superstore chains for false and misleading information on the systems they were selling. The sales people were telling their customers that the systems were Y2K ready when they knew that they were not, just to make sales!
The October article, the fourth in the series, was about Microsoft operating systems. I tried to be fair, but a few people felt that I was too hard on Microsoft about Windows 98. As it turns out, Windows 98 has several more faults than even I listed. In late November, then again in early December, Microsoft issued a service patch for Windows 98 to fix the Y2K and other problems in the new operating system. The article discussed Windows NT 4.0 and the real time clock(RTC) problem. In December, the RTC problem was found to be a major problem for DOS since it accesses the RTC for many DOS functions. Gee, just what Microsoft said would happen. This is why you should consider upgrading to a newer operating system.
The last article in the combined November/December newsletter discussed applications. I had two people who were upset because I stated that Microsoft was selling the Office 97 service releases on CD-ROM. When I wrote the article I had the FAX from Microsoft stating not only how to order the CD-ROM disks but how much they would cost. Well, Microsoft changed their minds between the time I wrote my article, and when your newsletter arrived in the mail. They decided to give the patches away. Who would have guessed it?
So much for the quick review of the past articles. Now let’s move on to this month’s article. Macros are a very useful tool to reduce the number of keystrokes it takes to complete repetitive operations. For the most part, macros are not a problem, especially those supplied by Microsoft in Office 97. Macros in Office 95 and earlier, I have not tested. Since the applications are not Y2K ready, I would suspect that the macros are not necessarilyY2K ready.
In Excel from Office 97, you are able to create macros by recording keystrokes one time and then replaying all the keystrokes by calling the macro. You have been able to do this in many earlier versions also. Macros created in Excel for Office 97 are Y2K compatible. Macros from earlier versions should also be compatible, but you need to test each one to be sure. Unless you have done some interesting programming, they should not be a problem.
Here is the first problem. If you have a document or spreadsheet that was first created in Office 95, then converted to Office 97, there could be a problem with the macro. I converted an old Office 4.3 document that had a date macro that I knew would fail, into Office 97. When the macro was run, instead of producing an automatic date for the next contact, you got XXXX in its place. Ok, you can live with this problem.
Here is the second problem. If you have had someone writing Visual BASIC macros, you have now opened Pandora’s box. Using Visual BASIC, a programmer can directly access the RTC in the computer. Visual BASIC can also calculate dates in spreadsheets that may not be Y2K compliant.
You may be surprised at what programmers have done using Visual BASIC. Recently I saw a macro in Excel from Office 4.3 used to create dates for a calendar. I checked the program with my system at home set to January 1, 2000 and found that it not only failed, it crashed Windows NT 4.0 operating my system. I had to reboot the computer!
I hope you see this can be a very simple problem if you do not use macros. If you use only macros supplied in Office 97, you should not have a problem. If you have upgraded from Office 95 or before, you need to check the macros to see if they work; it is not hard to do and you know quickly. If you have custom Visual BASIC programs, you can have problems.
Now let’s move to Corel Office Suite 7 and 8. Office Suite 7 is not Y2K ready because of how it handles printing. I have not been able to break any of the supplied macros with Office Suite 7 or Office Suite 8. Corel is not planning to issue any patches to Office 7; they want you to upgrade to Office Suite 8.
This does not mean that you are now out of the woods. I checked on the Internet and found over 300 sites with macros for WordPerfect. There is no way I can say that any of those macros are Y2K ready or not. They do everything from reformatting your document to calling other programs to check your grammar.
This article is getting long, so I am going to move data conversion to be Y2K ready, to next month. The February article will start a series of articles on some suggestions to get you and your family ready for Y2K. It will be simple things that you can do to be ready if the “worst case” scenarios happen. If you have any questions or comments about this series on Y2K, you can contact me at jonslough@tln.net or at my new EPCUG Email address at jonslough@epcug.org. I will also be on the new mail list for EPCUG members. Remember you must be a member of EPCUG to be on the mailing list and we will not allow spamming in our mail group.
 Top
Top
In response to a call from Jocelyne Slough about a CD-Rom being offered by Microsoft on Year 2000 issues, I went to the site that she first recommended. An article on NEWS.COM (http://www.news.com/) has information about the Microsoft free cd’s.
Microsoft offers Y2K tools package
By Erich Luening and Kim Girard
January 7, 1999, 8:25 a.m. PT
http://www.news.com/News/Item/0%2C4%2C30636%2C00.html?sas.mail
I followed this up with a call to the phone number listed within the article to order the CD. I first learned that the CD is not ready yet, but I did put my name on the list to receive one. I then asked a few questions about it so I could fill you readers in.
The CD is intended for those without internet access or very slow access, but others will not be denied ordering it. At this point the best indication I got from the operator was that the NEWS.COM article is pretty accurate, although the information was released to them a bit prematurely. It would appear that this will be a quarterly reissued CD (since it is called a ‘subscription’) and there was nothing in her information about a mailing cost to receive the CD, but I know that something like that is always subject to change. The content of the CD will basically be the contents of the web site, with any patches, updates, white papers, news articles, or other information that can be obtained by logging on there. If the subscription idea pans out, I would then assume that the next issue (presumably released 3 months after the first is received) would contain additional updates and patches as they are developed.
The phone number in the article will also get you in touch with an operator who can access any of the information on Microsoft’s Year 2000 web site, such as which products have a patch or update, and which are in line to receive one in the future. Any information within any of the published white papers (information articles) that have been posted on the site can be accessed by the operator and the information can either be read or faxed to the caller. Callers need to remember that this is NOT a technical support line, although if you need help, they may be able to tell you where to call and get it. Just don’t try to get *them* to help you fix the problem.
I also took a few minutes to look around Microsoft’s Year 2000 site itself, and was pleased with the contents. One page in particular was nice to see since it was not a self-centered (Microsoft-wise) page. The page lists any company which ask to be listed that offer Year 2000 remediation tools. While Microsoft does not endorse the company nor it’s products, I think it is really a great help to end users and corporations in their Year 2000 remediation efforts.
Another page lists services from Microsoft partners. “These services look at both Microsoft and non-Microsoft platforms so that your existing applications can be evaluated no matter what operating environment they are currently running on.”
No site would be complete without a ‘FAQ’ page, and Microsoft has 20 questions answered at this time.
And of course there is the product guide page which contains Microsoft Year 2000 Test Criteria, Recent Updates on Microsoft Products, and Microsoft lists products into 5 categories:
1. Compliant: The product fully meets Microsoft’s standard of compliance. May have prerequisite patch or service pack for compliance.
2. Compliant with minor issues: The product meets Microsoft’s standard of compliance with some disclosed exceptions that constitute minor date issues.
3. Not Compliant: The product does not meet Microsoft’s standard of compliance.
4. Testing yet to be completed: Product test is not yet complete or has not been started but will be tested.
5. Will not test: The product will not be tested for compliance.
Be sure to read the NEW.COM article, and spend some time on Microsoft’s Y2K site. I think it will be enlightening for you. (And thank you, Jocelyne :)
http://www.microsoft.com/technet/topics/year2k/default.htm
 Top
Top
Press Release
http://www.y2k.gov/new/0107PRLS.htm
New Toll-Free Line Provides
Y2K Information to Consumers
1-888-USA-4-Y2K
Assessment Summary Report Web Information Help Answer Questions About the Year 2000 Computer Problem
The President’s Council on Year 2000 Conversion today introduced 1-888-USA-4-Y2K, a new toll-free Y2K information line, and other Council initiatives for providing consumers information about the Year 2000 (Y2K) computer problem.
Council Chair John A. Koskinen joined Jodie Bernstein, Director of the Federal Trade Commission’s (FTC) Bureau of Consumer Protection, and Sara Cooper, Executive Vice President of the National Consumers League, at an FTC press conference to launch the information line, which will be supported by the General Services Administration’s Federal Information Center (FIC) and the FTC.
“This toll-free line is a key part of our ongoing efforts to make available information that will help Americans respond appropriately to the Y2K problem as we move through this year,” said Koskinen. “We are committed to providing consumers the latest information on how the problem may, or may not, affect government services, banks, household appliances, and other things they depend upon in their daily lives.”
1-888-USA-4-Y2K offers information of interest to consumers in common areas such as power, telephones, banking, government programs, and household products. Information for the line comes from primary sources — government agencies, companies, or industry groups. Pre-recorded information, which is available seven days a week, 24 hours a day, is available on the most common topics, and information specialists supported by researchers are available to provide additional information to callers. Information specialists will staff the line from 9 a.m. to 8 p.m. (EST), Monday - Friday.
“Consumers who want to know how computers in the Year 2000 will continue to deliver Social Security checks or how airlines will handle the Y2K problem now have a new tool,” said Jodie Bernstein, Director of the FTC’s Bureau of Consumer Protection. “The FTC is pleased to work with the President’s Council and the FIC to provide this information. 1-888-USA-4-Y2K will provide timely, accurate information on how computers will be able to deliver goods and services in the Year 2000.”
At the end of the month, the FIC will make available a “fax-on-demand” system, to provide callers with printed information on the Y2K problem at the touch of a telephone button.
The Council also announced two other initiatives for providing Y2K information to consumers: the release of its first quarterly summary report on industry assessments of Y2K progress and the creation of a special consumer information area on the Council’s web site.
The quarterly report, the first of four the Council will release in 1999, provides summaries of existing industry assessments for key areas such as communications and finance as well as information on public sector Y2K efforts. These assessments, the bulk of which come from major industry trade associations, are being gathered by the Council’s more than 25 working groups; many industry trade associations are in the early stages of gathering information from their members.
“Based on the data we have seen thus far, we are increasingly confident that there will not be large-scale disruptions among banks and in the power and telecommunications industries,” said Koskinen. “But one thing is clear: everyone has a lot of work left to do. We are most concerned about organizations that don’t have the Y2K problem as a high priority. They are the source of our greatest risk.”
Progress among some smaller governments and businesses remains a concern. And despite an increase in activity in other countries, international failures are likely and could have a significant impact upon areas that rely heavily upon cross-border operations.
The Council is working to ensure that the assessments summarized in the report are available in their entirety through its web site at www.y2k.gov. The next summary report is scheduled for release in April 1999, but individual assessments will be released to the public in the interim as they become available.
The Council has also expanded its web site, creating a separate area devoted entirely to consumer issues and the Year 2000 problem. This portion of the site contains information similar to that which is available on the toll-free line, but enables users to go one step further and link directly to the agencies, companies, and industry groups that are the primary sources for much of the existing information on Y2K efforts.
The FTC has three publications for consumers on Y2K: one on consumer electronic products, one on home office equipment and one on personal finances. These publications are available online from the FTC at www.ftc.gov and through the FTC’s Consumer Response Center, 202-FTC-HELP. The FTC also has a Business Fact Sheet urging businesses to disclose the Y2K status of their products to their customers.
The President’s Council on Year 2000 Conversion, established on February 4, 1998 by Executive Order 13073, is responsible for coordinating the Federal Government’s efforts to address the Year 2000 problem. The Council’s more than 30 member agencies are working to promote action on the problem and to offer support to public and private sector organizations within their policy areas. Visit the Council via the Internet at www.y2k.gov.
 Top
Top
“Oops!” One of the worst things you can utter while sitting at your computer, particularly if you’ve mistakenly deleted a necessary file or (worse yet) formatted a disk with data on it. Last month we looked at how to recover from deletions of files. This month, something even worse — accidental formats.
FORMAT and UNFORMAT
Reformatting your hard drive accidently is perhaps the worst Oops! you can make, since it has the highest potential for damage — losing everything. There are a few safety nets in FORMAT, plus a few you can put in yourself. If disaster strikes, you can try to recover with UNFORMAT, which may be successful depending on how the FORMAT was done.
FORMAT prepares a disk for use by “initializing” the surface; creating the sectors, File Allocation Table (FAT), and directory; and checking for and marking bad sectors so they are not used. Every new disk has to be formatted, including the hard disk in your computer. Typically that is done at the factory and you don’t have to worry about it — the worry is in reformatting the disk accidently.
A good analogy for what happens during a format is to think about a developer building a new subdivision out in the country. An unformatted disk is like undeveloped land, with random hills, gullies, and maybe a few random dirt roads. The first thing the developer does is flatten out the property, subdivide it into regular-sized lots, and build a series of roads leading to each lot. The developer then builds an office, and puts a map of the development on the wall. Maybe a few of the lots have swampy land and can’t be built on; these are crossed off the map so that they won’t be sold. As people start purchasing the lots, the developer crosses them off the map one by one.
The disk from the factory is just one large surface with random bits and bytes on it. Formatting takes the disk and divides it into uniform sectors for use in storing files. The random magnetic hills and valleys are smoothed out, and the underlying maps and structures (like the Directory and FAT) are created. Any “bad” sectors unfit for holding data are marked.
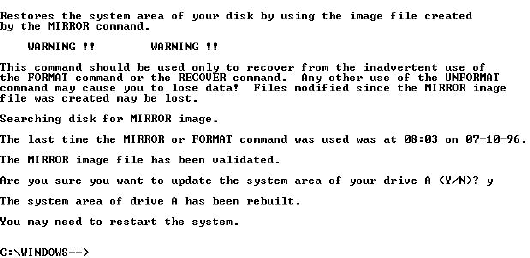
Continuing the analogy, reformatting a disk that currently contains files is like SERIOUS urban renewal: the bulldozers come in and flatten everything in their path. All the old buildings and roads are destroyed, and replaced with new vacant lots and new roads. A map of the area shows there is nothing left.
One of the best enhancements in DOS 5.0 was the “safe” format, which is now the default if you specify no switches on the FORMAT command line. If you format a previously formatted disk, FORMAT will save the FAT and root directory information in a hidden file (called the MIRROR file) on the disk. The FAT and root directory are then erased, but the data itself is not deleted or physically overwritten. The UNFORMAT command uses this MIRROR file to completely restore the disk - if new data isn’t written to the disk meanwhile. So the rule is, if you accidentally format a disk, UNFORMAT ASAP.
However, the FORMAT command includes a /U Unconditional switch, which does NOT save the MIRROR file and completely destroys all data on the disk. You can never UNFORMAT a disk that has been formatted with /U (at least through DOS; some disaster recovery companies have specialized hardware and software that can sometimes bring back an unconditionally formatted disk.)
Similar to a safe format is the Quick format, which occurs when you FORMAT with the /Q switch. The Quick format also saves a copy of the FAT and root directory to a hidden MIRROR file, but does not scan the disk for bad areas (which the default safe format does). Only do a Quick format on previously formatted disks you know are in good condition. If the disk has not been previously formatted, an unconditional format will be done.
There are a couple of safety nets in FORMAT to prevent an unintentional hard disk format. Starting with DOS 4.0, you had to explicitly enter the drive identifier of the drive to format. As far back as DOS 3.0 you got an error message if you try to run FORMAT on a hard disk:
WARNING, ALL DATA IN NON-REMOVABLE DISK DRIVE C: WILL BE LOST!
Proceed with format (Y/N)?
You have to explicitly type in Y to start the format.
As an additional precaution, starting with DOS 3.3 you must enter the volume label of the hard drive for the format to occur. Unfortunately, if your hard disk doesn’t have a volume label and you simply press [ENTER] when prompted for the label, blank matches blank and the format will begin. So your first and easiest protection against an accidental format is to use the LABEL command (LABEL C:) to put a volume label on every hard disk in your system.
For even more protection, include the NULL character (ASCII 255) as part of the volume label. You enter NULL by holding down the ALT key and typing 255 on the numeric keypad. The NULL will look like a space, but is a different character to DOS. Anyone trying to maliciously format the hard disk will probably type in a space instead of the NULL since they appear the same. But the labels won’t match so the format won’t proceed.
Another option is to rename FORMAT.COM to something less noticeable to others and know only to yourself. Or again you could use the NULL character to rename FORMAT.COM to
FORMAT<255>.COM, so that to use the command someone would have to enter the ASCII 255 from the keypad. Another option is to use DOSKEY to redefine “FORMAT” to run some other program, say DIR:
DOSKEY FORMAT=DIR
This in minimal protection against a nasty but knowledgeable person; they would know that by simply entering a space before FORMAT the original program would run and not the DOSKEY redefinition.
Windows 3.1x and Windows 95 offer some additional FORMAT safety. In Windows 3.1 File Manager, under Disk | Format, you only have the option to format floppy disks. In Windows 95 Explorer you can right-click on a Hard Drive and select Format, but you cannot format a disk containing open files, including the drive where Windows 95 resides (typically your boot drive). Windows 95 will also not let you format the host drive for a mounted compressed drive. However, in Windows 95 you can run FORMAT.COM from the DOS command line; WIN95’s FORMAT works exactly the same as in MS-DOS 6.x.
UNFORMATing a Disk
So what if, despite all your protection, you accidently format a disk? Run UNFORMAT as soon as possible. If you’ve reformatted your hard drive (boot drive), you will need to boot from a floppy and run UNFORMAT from the floppy — so have such an Emergency Boot Disk available.
When you run UNFORMAT against a disk that has a MIRROR file (in other words, it wasn’t unconditionally formatted with the /U switch), it restores the former root directory and FAT. As long as nothing has been written to the disk since the reformat, you will completely restore the disk. If data has been added to the disk, some original files may have been overwritten and are lost. Even so, you will still get back some data.
If UNFORMAT cannot find a MIRROR file, it attempts to rebuild the disk’s directory structure from the subdirectories. It cannot determine the names of the first level subdirectories (directly under the root), so it generically names them SUBDIR.1, SUBDIR.2, etc. It then tries to restore the files from the subdirectories; files in the root directory can’t be recovered. If files are fragmented then cannot be recovered, since UNFORMAT can’t location the other parts of the file. You’ll have the option of truncating these files or deleting them completely.
Like UNDELETE, the UNFORMAT command was removed from Windows 95. However, you can still use UNFORMAT.COM from MS-DOS 6.x, which will be in your original \DOS directory.

Although accidently deleting files or formatting your hard disk are serious, as you’ve seen there are some things you can do to allow you to prepare for, and prevent disaster. So instead of saying “Oops!” you can say “Oops! But No Problem!”
Kenneth E. Johnson is Assistant Editor of the American Bar Association’s Network 2d newsletter and Contributing Editor of DOS World Magazine. His book on Web authoring for attorneys will be published by the ABA in the spring of 1997. He is also a coauthor of WordPerfect Law Office Solutions for DOS and of WordPerfect law Office Solutions for Windows.
 Top
Top
This page was prepared by Pam Hystad, 1998-12-11, with permission of the author.
This document may be copied, in its entirety, for non-commercial or personal use; all rights are reserved by Jo Anne Slaven, 1998.
The Jo Anne Effect was named by Cory Hamasaki after Jo Anne Slaven, who first identified the problem and wrote about it in the newsgroup comp.software.year-2000.
The Jo Anne Effect is about accounting and fiscal year-end problems. Many companies have a fiscal year that spans two calendar years. For example, the fiscal year may start on February 1 and run through to January 31. Companies in the retail sector often use this particular reporting period, since their inventory levels and sales activity are lowest at this time of the year.
When a company follows a fiscal year spanning two calendar years, and non-compliant hardware or software is being used in the accounting department, some problems could crop up when they attempt to “close the books” for fiscal ’99 and “open the books” for fiscal ’00. Depending on the type of hardware and software in use, the following might occur:
On attempting to “close” fiscal ’99 and “open” fiscal ’00, the system may return an error message indicating that the date for the new fiscal year-end is invalid. This will make it impossible to process any accounting transactions in the new fiscal year.
Fiscal ’99 may close properly, but fiscal ’00 may sort incorrectly. What comes first - 02/01/99 or 01/01/00? In what month will the February 1999 transactions (sales, etc) be recorded?
The roll-over to fiscal ’00 may appear to go smoothly, and the dates may seem to sort correctly, but some transactions may be “lost” or incorrectly recorded. Accounts receivable transactions, for example, with a due date in 2000, might disappear entirely.
The Jo Anne Effect is not expected to cause problems that will shut down corporations overnight. It is, however, expected to cause enough small difficulties to cause companies to recognize the Y2k threat and to speed up their Y2k remediation efforts.
 Top
Top
If not, go to the EPCUG home page and click on the mailing list link, or go directly to the signup page at:
Fill out the form and then FOLLOW THE INSTRUCTIONS on the ThankYou page which you will be sent to when you submit the form.
The EPCUG Mailing List is set up to aid EPCUG members in helping each other, and for occasional messages from the Board of Directors. A place to ask questions, share news, and discuss other computer related topics.
If you have JUNO or the web page does not work for you (some older versions of AOL don’t). Send an email directly to the list manager at:
Put the word SUBSCRIBE in the subject line AND the body, and be sure to include your name and address in the body.
(Note: this is different than last month’s article. It said to send it to the wrong address.)
 Top
Top
The wonderful world of computers is truly a fascinating place, but it is also a place where a lot of people are doing their very best to separate consumers from their money. As a result of a study in which the Federal Trade Commission asked people to send them their junk e-mail, the FTC has identified the 12 scams that are most likely to arrive in consumers’ e-mail boxes.
1. Business opportunities
These business opportunities make it sound easy to start a business that will bring lots of income without much work or cash outlay.
The scam: Many of these are illegal pyramid schemes masquerading as legitimate opportunities to earn money.
2. Bulk e-mail
Bulk e-mail solicitations offer to sell you lists of e-mail addresses, by the millions, to which you can send your own bulk solicitations.
The problem: Sending bulk e-mail violates the terms of service of most ISPs. Several states have laws regulating the sending of unsolicited commercial e-mail, which you may unwittingly violate by sending bulk e-mail.
3. Chain letters
You’re asked to send a small amount of money ($5 to $20) to each of four or five names on a list, replace one of the names on the list with your own, and then forward the revised message via bulk e-mail.
The scam: Chain letters — traditional or high-tech — are almost always illegal, and nearly all of the people who participate in them lose their money. The fact that a “product” such as a report on how to make money fast, a mailing list, or a recipe may be changing hands in the transaction does not change the legality of these schemes.
4. Work-at-home schemes
Envelope-stuffing solicitations promise steady income for minimal labor, e.g., you’ll earn $2 each time you fold a brochure and seal it in an envelope.
The scam: You’ll pay a small fee to get started in the envelope-stuffing business. Then, you’ll get instructions on how to send the same envelope-stuffing ad in your own bulk e-mailings. If you earn any money, it will be from others who fall for the scheme you’re perpetuating.
5. Health and diet scams
Pills that let you lose weight without exercising or changing your diet, herbal formulas that liquefy your fat cells so that they are absorbed by your body, and cures for impotence and hair loss are among the scams flooding e-mail boxes.
The scam: These gimmicks don’t work.
6. Effortless income
The trendiest get-rich-quick schemes offer unlimited profits exchanging money on world currency markets, newsletters describing a variety of easy-money opportunities, the perfect sales letter; and the secret to making $4,000 in one day.
The scam: If these systems worked, wouldn’t everyone be using them?
7. Free goods
Some e-mail messages offer valuable goods — computers, other electronic items, and long-distance phone cards — for free.
The scam: Most of these messages are covering up pyramid schemes, operations that inevitably collapse.
8. Investment opportunities
Investment schemes promise outrageously high rates of return with no risk.
The scam: Ponzi schemes eventually collapse because there isn’t enough money coming in to continue simulating earnings. Other schemes are a good investment for the promoters, but not for the participants.
9. Cable descrambler kits
For a small sum of money, you can buy a kit to assemble a cable descrambler that supposedly allows you to receive cable television transmissions without paying any subscription fee.
The scam: The device that you build probably won’t work. Even if it worked, stealing service from a cable television company is illegal.
10. Guaranteed loans or credit, on easy terms
Some e-mail messages offer home-equity loans that don’t require equity in your home, as well as solicitations for guaranteed, unsecured credit cards, regardless of your credit history.
The scams: The home equity loans turn out to be useless lists of lenders who will turn you down if you don’t meet their qualifications. The promised credit cards never come through, and the pyramid money-making schemes always collapse.
11. Credit repair
Credit repair scams offer to erase accurate negative information from your credit file so you can qualify for a credit card, auto loan, home mortgage, or a job.
The scam: The scam artists who promote these services can’t deliver. The promoters also may be encouraging you to violate federal law. 12. Vacation prize promotions
Electronic certificates congratulating you on “winning” a fabulous vacation for a very attractive price are among the scams arriving in your e-mail.
The scam: Often, the cruise ship you’re booked on may look more like a tug boat. The hotel accommodations likely are shabby, and you may be required to pay more for an upgrade. Scheduling the vacation at the time you want it also may require an additional fee.
I commend the FTC for doing such a good job of compiling this list. I encourage all readers to be very careful when responding to offers they receive over the Internet.
About the Author: We continue to enjoy Frank Vaughan on our pages. Frank is a Computer Bits’ magazine editor-at-large. Computer Bits’ Online and information regarding their print edition subscriptions can be found at http://www.ComputerBits.com/
This article is reprinted in the Elkhart PC Users Group by express permission from Frank Vaughan and is not to be included in any article exchange agreement EPCUG may have with any other publication or organization. Any reprint requests for this article must be directed to Mr. Vaughan. E-mail to frankv@computerbits.com.
This article was originally published in the November 1998, Volume 8, Number 11 issue of Computer Bits magazine, and is copyright 1998 by Bitwise Productions, Inc., Forest Grove, OR, (503) 359-9107. All rights reserved.
 Top
Top

Some months back I wrote two articles (Keep It Clean, Parts 1 & 2) about the importance of keeping your computer clean to keep it operating properly. They obviously struck a nerve because they have been among the most widely reprinted and requested Ken’s Korner columns to date.
I just had an experience that underscored the cleanliness message, one that involved a vital part of any computer system: the mouse or other pointing device. Since those earlier articles didn’t cover the care and cleaning of mice, I thought it would be good to share my experience with you.
(Actually, I use a Logitech TrackMan trackball, not a mouse, but the problem and cleaning procedure outlined below are similar for either type of pointing device.)
Over a period of several weeks I noticed the trackball was getting balkier, making it harder and harder to drag the cursor into position. Finally it got so bad I had to struggle to move the cursor at all. “Oh-oh,” I said to myself, “ I hope it’s not time to buy a new trackball.” The Logitech device was several years old and had been used a lot, so I thought it might well need replacement. Then I remembered the mantra that Dennis Orloff of the ComputerBath line of maintenance products (www.computerbath.com) chants at every opportunity: “It’s not broken, it’s dirty!
Since he’s right about 70% of the time, I decided to check first to see whether the trackball was just dirty. When I took it apart I was amazed at how much dirt had accumulated inside the poor critter. It wasn’t just dust or loose dirt, either. There was a buildup of grime and a sort of lint, especially around the small ball contacts or rollers inside the ball cage. It was obvious that the crud was keeping the trackball marble from making proper contact with the rollers. The result, difficulty in moving the cursor, would be the same for an equally dirty mouse.
I cleaned everything thoroughly, and presto...it was like I had a brand-new trackball! Here was more proof of the need for keeping things clean as part of computer maintenance.
The procedure was simple, took just about 10 or 15 minutes, and saved me some bucks. So it’s worth your while to see if cleaning will fix a balky pointing device before you toss it out and buy a new one. What you really should do, in fact, is clean your mouse or trackball periodically, and not wait for it to get as dirty and hard to use as mine was.
Here’s how you do it.
First, if you have a manual for your mouse or trackball, dig it out. (Note: You should always keep manuals and documents for ALL hardware and software.) Read it. It may show a diagram or cutaway, and possibly instructions, that will make the cleaning job easier for you. The only tool you may need is a small screwdriver, probably a phillips-head type; you will also need a clean, lint-free cloth, Q-Tips or similar cotton swabs and a mild soap solution. Small tweezers, isopropyl (rubbing) alcohol and a toothpick may be useful, too . I find it convenient for jobs like this to keep screws and other small parts in an old ashtray, which also can serve as a tool rest.
Next, clean the mouse or trackball exterior and cord with a cloth moistened in a mild soap solution; wipe dry. Then turn the device upside down and remove mouse ball retainer plate or trackball bottom cover. Usually the retainer plate can simply be rotated and lifted out. Some older mice and most trackballs have screws holding the plate or bottom cover in place. Remove the ball carefully.
Clean ball with the moistened cloth, wipe with dry cloth and set it aside. (Make sure it is completely dry before reassembling.) I blew loose dirt out of the ball cage with a compressed air duster, held some distance away to lessen the impact. Be careful here so that you don’t damage any components. In my case, I had to use a toothpick and tweezers to dislodge some of the matted lint around the contacts in the ball cage. A cotton swab lightly moistened with alcohol may also be helpful for cleaning rollers or contacts and the inside of the ball cage.
When cleaning mice, take a close look at the rollers inside. (Most have three, some just two.) You will probably see dark lines of dirt that have built up over time. Work a cotton swab moistened just slightly with rubbing alcohol along each roller, rubbing side to side until the line of dirt is gone.
Once everything is squeaky clean, place the ball back in the ball cage and replace the retainer plate or bottom cover. That’s it; you’re done, and your mouse or trackball should be as good as new.
Copyright 1998 by Ken Fermoyle, Fermoyle Publications.
Ken Fermoyle has written some 2,500 articles for publications ranging from Playboy, PC World and Popular Science to MacWeek and Microtimes. He was cohost/producer of a radio show on computers and a partner in a DTP service bureau during the ’80s. Ken’s Korner articles are available free to User Group newsletters and Websites. For permission to reprint this article or to receive the column monthly, contact: kfermoyle@earthlink.net.
 Top
Top
We are hoping to continue the practice of placing an asterik on your label if your membership is about to expire. As with many people, they just never think about signing that sheet, their main purpose is to get into the meeting, get a seat, and prepare to hear the presentation. This is fine, BUT! You do need to make sure you sign the sheet atleast once or twice a year to make sure you keep updated on the membership list.
For those of you who sign the sheet *EVERY* month, I would like to make a suggestion. While this doesn’t hurt anything, it really isn’t necessary. It does cause the Membership Director to become very familiar with your name, as I get to see and check it off each time you sign. On the other hand, it does take extra time. Please consider signing the sheets just every few months.
Remember, once a year is sufficient to keep you on the lists. Now, if it were me, I might forget when I last did, if I tried to only do it once a year. So, maybe a few times as opposed to every time, might be a good idea.
For right now, you should be able to check your mailing label and make a special effort to check your name when an asterik appears. You will have 2 meetings after the asterik FIRST appears to get updated. I hope this helps and that you appreciate the extra efforts involved to maintain it this way.
Note: This is the 2nd month we have been doing this. Pull out last month’s issue to see if you are showing your asterik for the 2nd time, and need to be sure to attend *this month’s* meeting, or contact the Membership Director:
Sherry L. Nisly
318 S 10th Street
Goshen IN 46528-3514
nisly@epcug.org
(219)533-6224
 Top
Top
Remember, you can volunteer to help out the current officers anytime. This organization will not continue to run with only a couple people doing all the work.
Have you done your fair share? Is there some small task you can help with? Even if it is only for a time or two, offer to help with one of their jobs.
Help the Membership Director work the front door at meetings. Offer to lead one of the SIG groups one month. Pick up some newsletters to deliver to a business or school that you pass each month.
Think about it, are you sure there isn’t something you can do? Can’t think of anything? Just ask, they probably have some small job in mind right now!
 Top
Top
Comments, corrections and suggestions to EPCUG Webeditor